I’ve stumbled upon a seemingly undocumented authentication error in the Windows VPN system.
Error 691: Access was denied because the username and/or password was invalid on the domain.
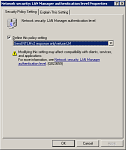
This can be caused simply by elevating the VPN server’s LM authentication level to 5, which refuses the NTLM protocol. According to KB823659 requiring NTLMv2 should not break Windows XP connections unless older systems are involved. However, this configuration does cause client and server authentication errors.
On the server side, the VPN error looks like this:
Event Type: Failure Audit
Event Source: Security
Event Category: Account Logon
Event ID: 680
User: NT AUTHORITY\SYSTEM
Description:
Logon attempt by: MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
Error Code: 0xC000006A
To resolve this problem, simply reduce the LM authentication level to 4, “Send NTLMv2 response only\refuse LM.”
Really great tip. I ran into exactly this problem when using RASDIAL tonight. Took me about an hour to find this post, which solved my problem. Thanks!!
This still causes issues with Windows 7 and Server 2012. Thanks for the post. Saved me a big headache.
Hi Sean, thank you for writing. I guess this is an oldie but goodie. I’ve updated the tags to include Server 2012. Enjoy your good as new VPN. ????